

MAGNET Beyond is a worldwide R&D project within
Mobile and Wireless Systems and Platforms Beyond 3G.
MAGNET Beyond will introduce new technologies, systems,
and applications that are at the same time user-centric
and secure. MAGNET Beyond will develop user-centric
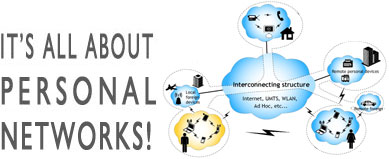
business model concepts for secure Personal Networks
in multi-network, multi-device, and multi-user environments.
MAGNET Beyond has 30 partners from 15 countries, among
these Industrial Partners, Universities, and Research Centres.
MAGNET Beyond is a continuation of the MAGNET project.
richard mille replica

Discover Bong Shop Australia, where smoking enthusiasts find the ultimate bongs to elevate their experience. Our diverse selection ensures every user can enjoy smooth hits and unique styles. Don’t miss out—check out our bongs for sell and transform your smoking sessions today!
Contact: Aalborg University · Niels Jernes Vej 10 · 9220 Aalborg East, Denmark · Phone: +45 96358080 · E-mail: [email protected]
IST-FP6-IP-027396 © MAGNET Beyond 2006-2008. All rights reserved.